Certified Red Team Expert (CRTE) Review
\x01 Introduction
Wow, it's been a while since I last posted something. Between life and studying, I haven't been able to devote a lot of time on posting. With that said, I am back to offer my review of the Certified Red Team Expert course by Altered Security (formally PentesterAcademy). I thoroughly enjoyed the course, the labs were fantastic, and the exam was very challenging but was a joy to work through and ultimately pass.
I signed up for the CRTE course right after passing CRTP because I wanted to keep the momentum up and pick up where the CRTP left off when it comes to more advanced tactics, techniques, and procedures. While there is some overlap between CRTP and CRTE, I believe CRTE does a great job at going a little deeper with various techniques and goes into more countermeasure bypasses.
Ok, cool - but what will you learn if you choose to go through the CRTE course? Well, let's see what AlteredSecurity says about it!
- Practice various attacks in a fully patched real world Windows environment with Server 2019 and SQL Server 2017 machines.
- Abuse Active Directory and Windows features like LAPS, gMSA, AD CS and more
- Execute and visualize the attack path used by the modern adversaries.
- Attack Azure AD Integration (Hybrid Identity).
- Try new TTPs in a fully functional AD environment.
- Understand defenses and their bypasses for (JEA, PAW, LAPS, Selective Authentication, Deception, App Allowlisting, Microsoft Defender for Identity etc.)
Various topics such as LAPS, gMSAs, ADCS, and Azure AD hybrid identity were a great addition as they were not covered in the CRTP and Nikhil did a fantastic job of going over what they are and how to leverage them to abuse AD. Nikhil also goes into detail about resource based constrained delegation which was a nice pickup from the previously covered delegation attacks in CRTP.
\x02 Course Pricing
Similar to CRTP, there are three different pricing tiers you can choose from when purchasing the course. The course itself is the same but comes down to how many days of lab time you want.

I personally went with the 90-day option because my life can be busy at times and I didn't want to rush through the course because I may not have the time to spend in the labs. Suffice to say, 90-days was PLENTY of time and actually as of writing this, I still have 5 days of lab time left and I took the exam almost a month ago.
Challenge Lab vs Bootcamp
When I purchased the course, I had the option of choosing either the red team challenge lab or recordings of the boot camp with the accompanying red team lab. I went with the recordings of a previous boot camp because previous CRTE reviews I read explained the boot camp covered additional material that the challenge lab didn't
After speaking with folks currently enrolled in the CRTE that chose the challenge lab track, this does not seem to be the case anymore. Sounds like Nikhil updated the course so both tracks cover the same exact material! The boot camp videos included roughly 14 hours of pre-recorded content to go through and covered everything you needed to know in order to compromise the entire lab environment.
\x03 My Thoughts on the Course
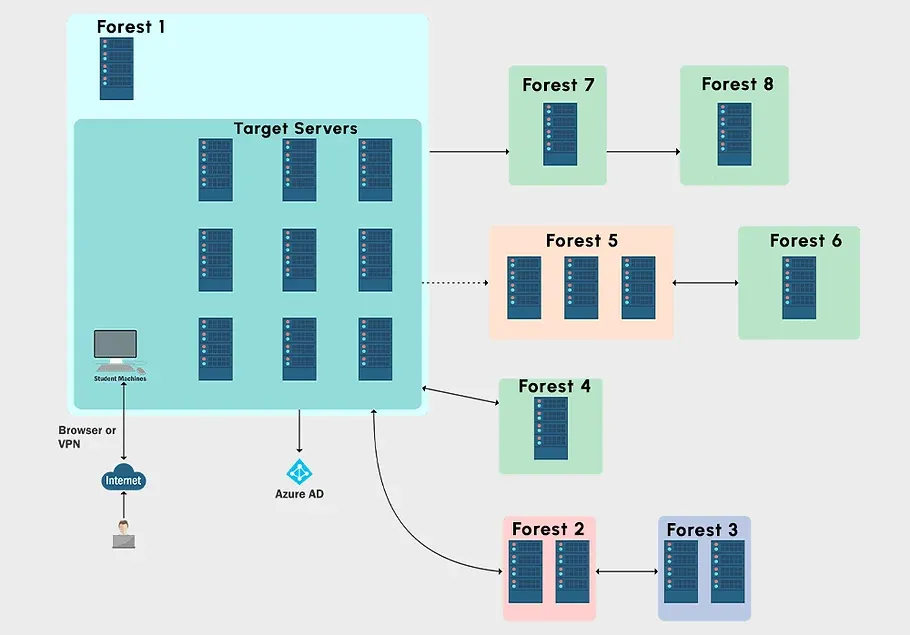
First off, the labs were arguably the best thing about the course. The lab consisted of numerous domains and forests all with various types of trust relationships and even had an Azure AD component that you had to enumerate and abuse. Below is what you can expect from the lab layout.
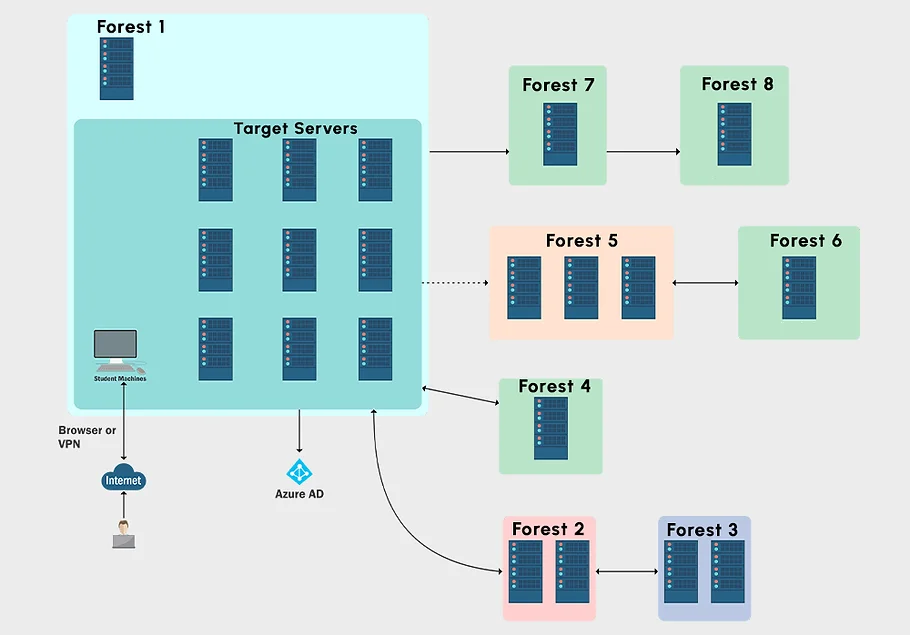
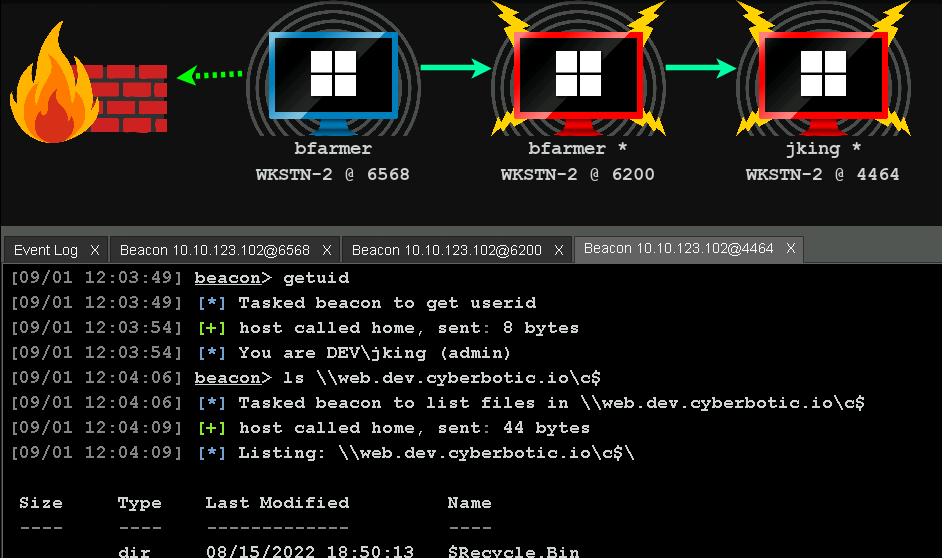
Since I chose the boot camp recordings option, the course was very similar to that of CRTP in that it's more of a walkthrough than a challenge lab. You aren't just dropped inside this massive lab environment and left to fend for yourself. Instead, Nikhil walks you through the steps of initial enumeration, local privilege escalation, domain enumeration, domain escalation and more. I personally enjoyed the format as it gave me time to watch how to do it, take proper notes, and perform what I had just learned in the lab environment.
Looking back at my course notes, the high-level topics that were covered were -
- Active Directory (this was more of a refresher than anything)
- Offensive Powershell
- Domain Enumeration
- Local Privilege Escalation
- PowerShell Remoting (and WinRS)
- Domain Privilege Escalation
- Lateral Movement
- Offensive .NET
- Domain Persistence
- Cross Trust Attacks
- Cross Forest Attacks
- Detection and Defense
Throughout the 14-hours of video content, Nikhil walks you through a plethora of abuse vectors ranging from kerberoasting, LAPS, gMSAs, Kerberos delegation (including RBCD), ADCS, Azure AD, FSPs, and more. You also have 60 verification flags you're hunting for while you work your way through the lab. Other than a few casual misspellings, I didn't find issues with the flags and knew what they were looking for.
Overall, I really enjoyed working my way through the lab environment and getting to leverage abuses that I haven't really had a chance to use up until now. It even covers AD CS which was a brand new topic for me. I highly recommend watching the SpectorOps presentation at Black Hat 2021 covering AD CS and its abuses - it's a great watch!
I started the course December 19th 2022 and wrapped up the final section the February 13th. If I can count correctly, that's 56 days going through the course material and the lab environment. If you already completed CRTP, I think 60 days of lab time should work just fine if you are unsure of how much time you can devote to the course.
Full transparency, I did run into a few occurrences where one of the domain controllers in the lab quit responding which made it so various tools that relied on them being up didn't work. In all of the occurrences, I reached out to the support team and they resolved the issue in less than an hour and I was back up and running. Other than that, the environment was perfect and didn't face any issues other than the DC going down.
Now - time to go over the exam...Dun dun duuuun!!
\x04 The Exam Experience
Obviously I cannot go into detail as to protect the integrity of the exam. However, I will try my best to outline the exam experience without giving away too much.
Just like CRTP, you can choose to start the exam when you feel you're ready as the exam is started through the student portal. After about 15 minutes of setup time, you're on your way! You have 48 hours to complete the exam objectives with another 48 hours to submit your professional-level exam report. You get your own exam environment that consists of a number of machines spread across multiple domains and forests.
Initial Kickoff
The exam started out pretty easy for me. I was able to spot what I had to do in order to compromise the student machine - which is the machine you land on at the start of the exam (since it's an assumed breach). From there, lateral movement to the first target machine was trivial and got access in the first 2 hours of my exam starting.
Enumerate Harder
From there - I hit a massive roadblock. I knew exactly what I had to do to make the jump to the second target machine, but the abuse that was required wasn't covered too much in the lab and required A LOT of enumeration, research, and trial and error to succeed. After what felt like 8 hours of trying, I compromised the second target box. I still have a headache from how long the jump took me, but it felt great getting pass it.
Ok - We're Good Now
The jump to the next target was pretty simple (if you know how to enumerate, that is) and in less than an hour, I compromised my next machine. At this point, I was stuck again. I knew I must have missed something in my enumeration and in BloodHound. Guess what? I did. All I can say is make sure you read all of the various nodes in BloodHound because if you don't, you will waste a lot of time for no reason. It was right in front of me the whole time and I missed it. Once I figured out what I had missed, my next target was down. At this point, the jump to the final machine was trivial, and after all of that, I was done! I compromised all of the machines in the exam environment and boy was I happy!
At this point, it was 5AM and I needed sleep before starting on my exam report. That's a tomorrow problem.
Exam Tips
- Report as you go! Read that again. Really, it makes a world of difference.
- If you want to use BloodHound, set it up locally before you start the exam. Ensure the version of the ingestor will work with your version of BloodHound!
- As great as BloodHound is, don't rely on it for everything. You need to know how to find things manually as well.
- Take good notes! Notate everything as you come across things in the exam as you don't know when you might need to go back to previous steps.
- Enumerate...enumerate...enumerate. Leave no stone unturned.
- Slow down. You have 48 hours to knock this thing out. Take time to eat, take a break and sleep.
- Have a report template dialed in before you start the exam.
\x05 Exam Report
Since I was reporting as I went through the exam, the majority of the report was already complete - well, at least the bulk of it. Really all I had to do was ensure I had all of my screenshots and supporting information such as remediation steps and references.
Another shout out to Report Ranger by the fantastic team over at Volkis. All you need to do is document each finding in a markdown file and Report Ranger will handle the rest and generate a PDF. Below is the GitLab link if you want to check it out 👇
Report Example
Report Ranger really saves the day when it comes to reporting. Reporting doesn't have to be difficut if you have the tools to make it easier. When everything was said and done, my report was 44 pages.

I did go into more detail about Report Ranger in my CRTP review. Feel free to check it out below.

The Volkis team is planning some great looking improvements to Report Ranger which will make it even better than it already is. The Report Ranger roadmap is below if you're curious.

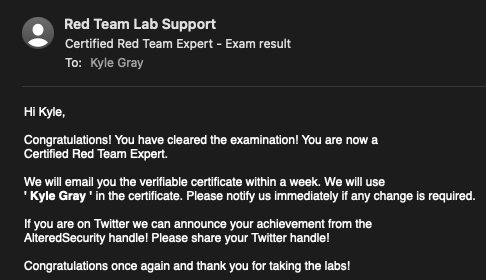
You cleared the exam!
I submitted my report to the lab team on February 19th and received an email saying they received it 27 minutes later. After waiting for a few days, I got my passing email on Feburary 25th. Let's go! 🙌
\x06 Wrapping Up
I really enjoyed the course, the lab, and oddly enough, the exam. CRTE did a great job at picking up where CRTP left off and covered more advanced topics. I can say what I learned in CRTE has already been applied in my professional work and that makes it worth it for me. Should you get CRTE? Yes. The course does an excellent job at covering various AD abuses and bypasses that can be leveraged to get around things like AV and MDI.
I recommend getting CRTP first then moving on to CRTE. Do you need to? No. However, CRTE is a perfect pick up from CRTP and expects you to understand the topics that were covered in CRTP. However, if you are familiar with red teaming and have experience, maybe jumping right into CRTE won't hurt.
So what's next? I don't know. I am thinking about going for CRTO after a little bit of a break before jumping right back into it. Always have to keep driving to hone my skill set and get better at my tradecraft.
Thank you for reading this long and probably long winded review! Until next time!